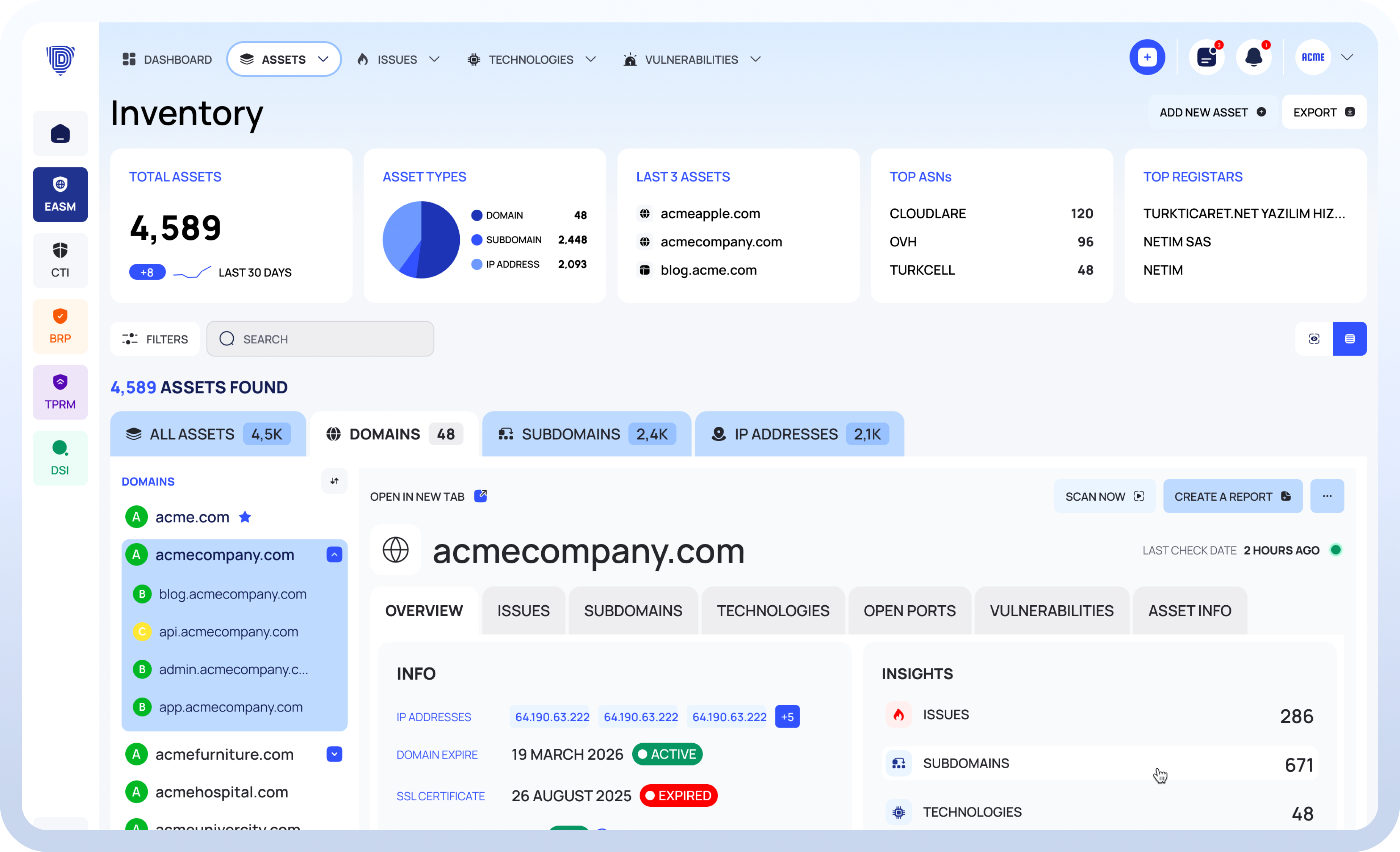
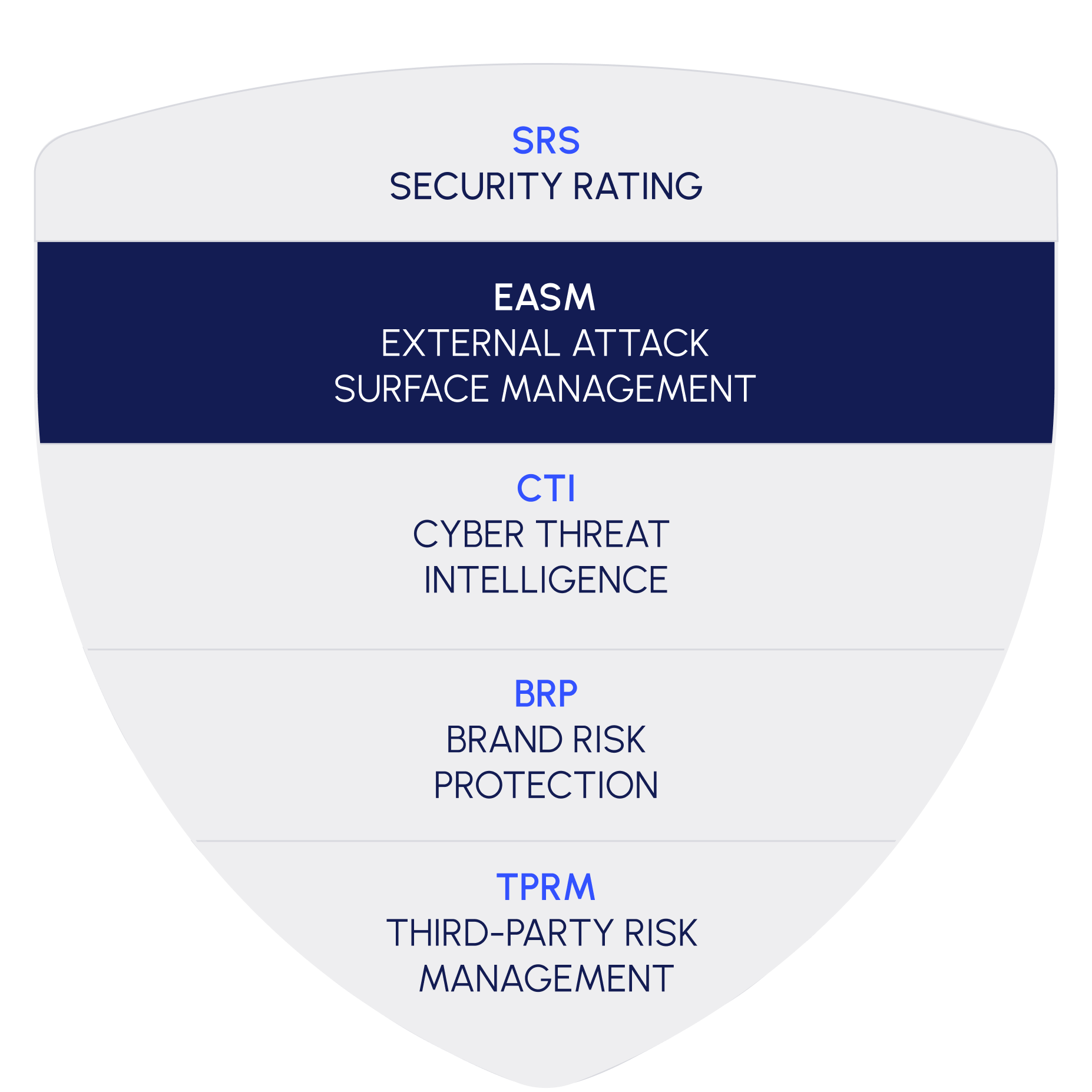
Continuous Threat Exposure Management Platform
Continuously detect, analyze, and mitigate threats across your digital landscape.

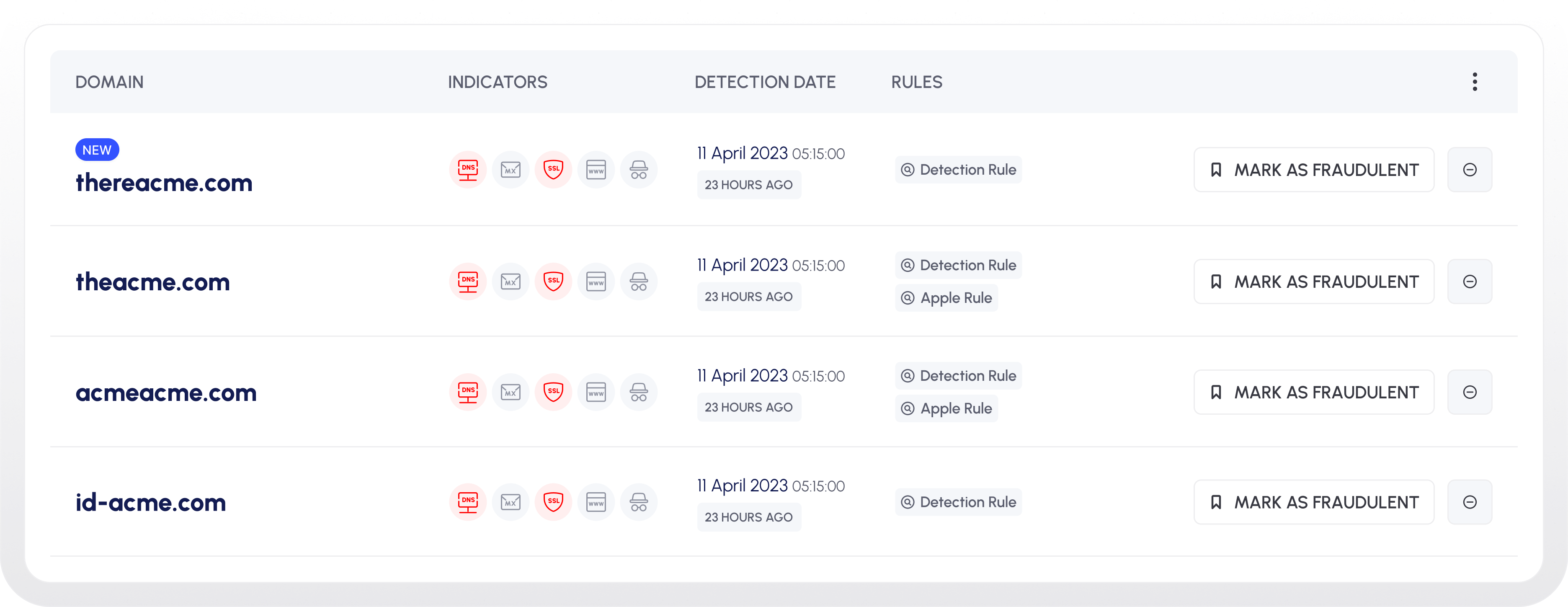
Cyber Threat Intelligence
Uncover Threats, Enhance Security.
SEARCH THE DARK WEB FOR THREATS
TRACK MENTIONS ACROSS THE DARK WEB
DETECT EMPLOYEE EMAIL BREACHES
IDENTIFY COMPROMISED EMPLOYEE DEVICES
FIND CLIENT CREDENTIALS IN BREACHES
DETECT EXPOSED PAYMENT INFORMATION
TRACK THREATS TARGETING EXECUTIVES
ANALYZE THREAT ACTORS & TACTICS
EXPLORE THE HISTORICAL BREACH INDEX


Trusted by organizations worldwide.














Request Demo
Trusted by leading companies worldwide, the Deepinfo Security Platform is the preferred choice for continuously managing cyber threat exposure.